IEC 62443 Standard
The IEC 62443 is the international cybersecurity standards framework for operational technology (OT). The framework consists of a collection of standards, technical reports and related information for securing Industrial Automation and Control Systems (IACS). The IEC 62443 provides all stakeholders involved in cybersecurity of IACS installations with guidance and a common basis for technical and organizational measures for increasing digital resilience. The framework of standards is visually represented below.
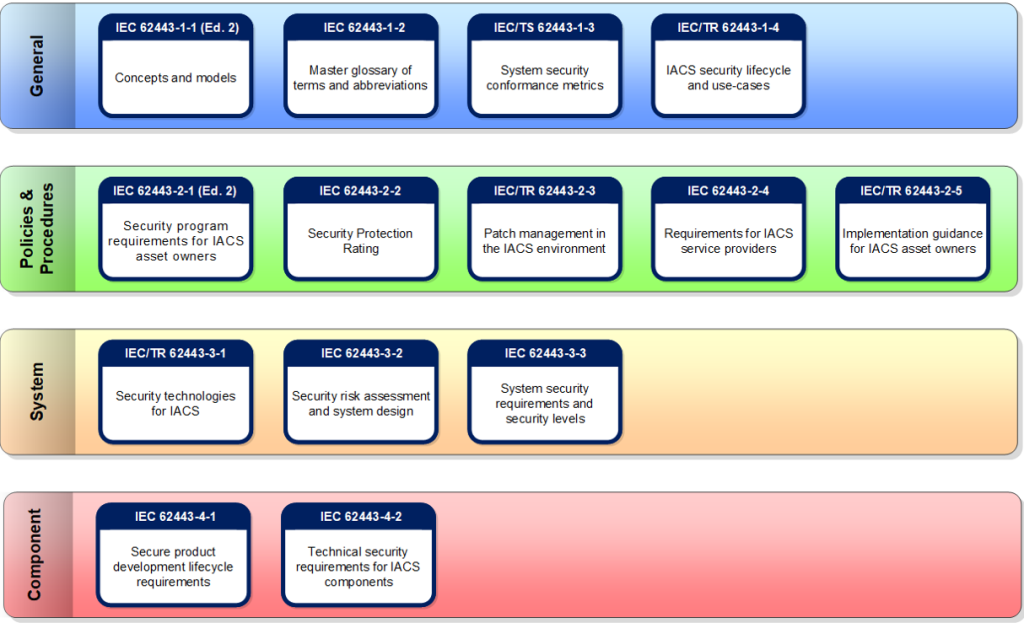
IT and OT are different disciplines. Besides similarities, there are also important differences. Within IT, confidentiality of information is essential, while within OT, aspects such as integrity and availability play a major role in aspects such as health, safety and environment. This makes it necessary to look at cybersecurity from a different perspective for both domains. Within IT, the ISO 27001/27002 is often used for information security. What the ISO27000 series is for IT, the IEC 62443 is for OT.

How is the IEC 62443 established?
The IEC 62443 is in fact a series of standards, technical reports, and related information that define procedures for securing Industrial Automation and Control Systems (IACS). These documents are the result of the IEC standards creation process where ANSI/ISA-62443 proposals (ISA99 Committee) and other inputs (like WIB) are submitted to country committees. The comments are reviewed by various IEC 62443 committees where those comments are discussed and, if necessary, changes are made. The IEC develops worldwide standards under the flag of the World Standards Cooperation, which includes the ISO and ITU as members.
